Internet Basics #6: Firewalls explained
- over 2 years ago
- 5 min read
Firewalls serve as the first line of defense in securing a network against potential cyberthreats. The term originated from the physical wall used to prevent the spread of fire within buildings. Similarly, in the digital world, firewalls aim to prevent the spread of harmful or suspicious traffic to devices connected to a network.
Understanding different security measures for networks is crucial whether you are an organization, a company or an individual operating in the digital landscape. In 2021, the US Federal Bureau of Investigation (FBI) recorded nearly 850,000 cybercrime complaints and a total amount of $6.9 billion lost to cybercrime. With cyberthreats on the rise, having a firewall in place is essential for protecting your network and devices. However, there are several types of firewalls alongside various firewall providers, and it can be challenging to determine which is best suited for your needs. In this Internet Basics Series post, we aim to clarify the types of firewalls and perhaps help you assess each of their relevance to your scenario.
The primary objective of a firewall is to permit safe traffic to enter the network while blocking potentially harmful traffic and thus ensure the security of connected devices and systems. Essentially all incoming and outgoing traffic will have to pass through a layer that evaluates each message and blocks those that don’t meet the set security requirements. Without a firewall, a device is more vulnerable to cyberthreats, such as hacking attempts and data theft. Someone could steal, delete or use your data to commit identity theft or financial fraud.
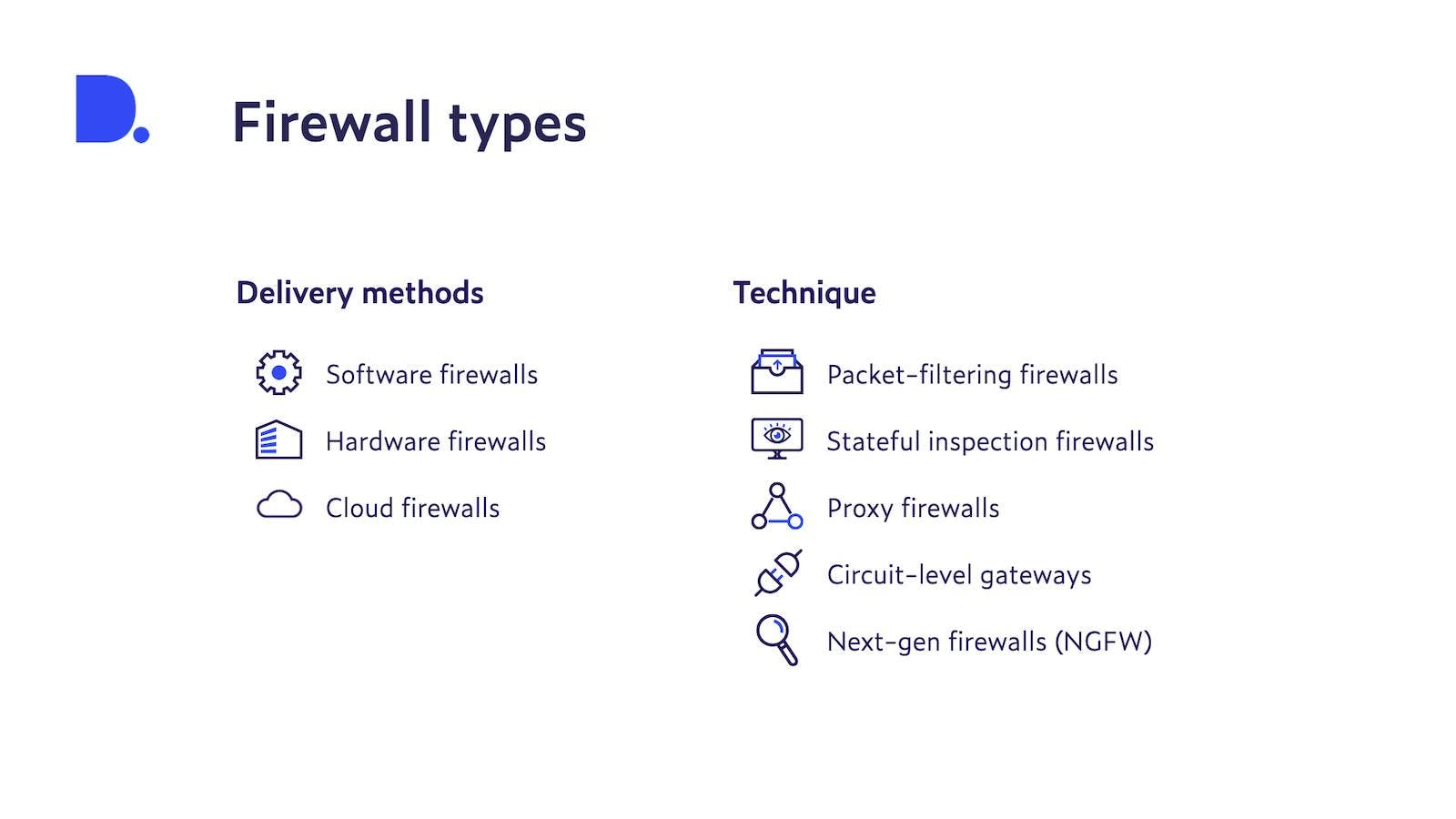
Firewalls can be divided into three categories based on delivery methods:
Software firewall
A software firewall, also known as a personal firewall, is installed on a single device, such as a computer, to protect against potential security threats to that device. Software firewalls can distinguish between different programs installed on a computer system. This means that a software firewall can, for example, differentiate between a web browser and a word processing software and apply specific security rules to each program. Most operating systems, such as macOS and Windows, include a built-in firewall. Often the built-in firewall does have to be enabled from system preferences.
Advantages of a software firewall include ease of maintenance, as well as ease of differentiation in levels of access and permission to users. Disadvantages include slow performance of the system due to using memory and disk space as well as required separate installation on each device.
Hardware firewall
A hardware firewall, on the contrary, is a physical device installed between the internet and a network. It is a stand-alone product that can be purchased and typically used on broadband routers. Hardware firewalls can be used as a border device or to segment and protect internal networks in larger enterprises.
Advantages of hardware firewalls include reduced latency, increased bandwidth and being less prone to cyberattacks due to running independently. Additionally, users can enable VPN (virtual private network) connections for increased security and encryption. Disadvantages include higher costs as well as required expert set-up and monitoring.
Cloud firewall
Cloud-based firewalls, also referred to as Firewall-as-a-Service (FWaaS) or Web Application Firewalls (WAF), are offered by many providers, including Amazon and Cloudflare, over the internet. These are software-based, cloud-deployed network devices typically operating within online application environments.
Cloud-based firewalls are becoming increasingly common due to the rise in remote work. Cloud firewalls can be easily integrated with cloud infrastructure, have high levels of availability, and no need for in-house hardware. The service provider also handles all administrative tasks. Disadvantages of cloud firewalls include privacy concerns and a lack of transparency due to third-party involvement.
How do firewalls operate?
A system with a firewall analyzes network traffic based on a predefined set of rules. The firewall will only allow incoming connections that conform to the established security protocols and reject those that don’t. Firewalls can be divided into five types based on their operating technique: packet-filtering firewalls, circuit-level gateways, stateful inspection firewalls, proxy firewalls and next-gen firewalls (NGFW). As the name suggests, NGFWs are a more recent development, while the rest are traditional firewall types that have been in use for many years. Each type of firewall can be deployed as hardware, software or in the cloud.
Depending on their design, firewalls can typically act on traffic at different layers of the TCP/IP (Transmission Control Protocol/Internet Protocol) protocol stack. Most internet applications, such as the world wide web or email, rely on this stack. In networking, packets are used to send data between computers. Packets have a header that gives information about IP addresses, protocol, source and destination ports. Computer applications are often associated with specific ports to communicate over a network. Incoming packets can thus be efficiently matched to the corresponding application. Packet-filtering firewalls act as a checkpoint to allow or block these packets based on a set of predefined rules. This firewall can, for example, be configured to block or allow certain ports to respectively block or allow specific applications to communicate over the network. More advanced configurations are also possible, such as only blocking a certain application when incoming packets originate from a specific IP address. Circuit-level gateways create a virtual circuit between the sender and receiver. Instead of examining packets, this firewall type verifies the connection (via a TCP handshake) and that the sender has permission to communicate with the receiver. Stateful inspection firewalls inspect packets at multiple levels combining packet inspection with TCP handshake verification.
However, there may still be ways for malicious traffic to pass through the previously listed firewalls. For example, communications over port 80 (for HTTP) may be allowed, and the connection may be valid, but if a packet arrives with malicious HTTP content it will not be blocked. This is where application-level firewalls come in. Application-level firewalls are able to understand specific application protocols, such as HTTP & HTTPS, and see if an allowed port is abused.
Proxy firewalls operate as a mediator between internal and external systems, protecting networks by masking client requests before sending them to the host. Finally, next-gen firewalls combine several functions of the aforementioned types of firewalls while adding advanced cybersecurity capabilities. NGFWs are commonly used in heavily regulated industries, such as healthcare or finance.
Which kind of firewall should you go for, then? Software firewalls are typically adequate for most individual users, as they provide essential protection against common threats. Configuring a firewall for business applications can be much more of a challenge due to the large number of computers on the network. For companies and organizations, the choice of firewall ultimately depends on the specific security needs and amount of network traffic.